As we emerge into a fresh new year, we asked technology, business, and industry thought leaders for their insights into the digital trends for 2025. And we’ve compiled their insights into AI, cybersecurity, cloud migration, regulatory compliance, open banking, and much more into a helpful guide that’s available now for download.
Experience the Looking Forward 2025 guide here.
As Axway CEO Roland Royer says,
“We like to think we have our fingers firmly on the pulse of data integration innovation. After all, we wouldn’t have made the choices that have made us a recognized leader in the digital marketplace if we didn’t.
So, we feel we’re in a decent position to extend some insightful observations on the upcoming year – and perhaps beyond – that could influence your own decision-making as you prepare your organization for a dynamic year ahead.”
But because this industry innovates so fast, it sometimes leaves in its wake an array of tech terms and acronyms that can make your head spin. To give you a taste of what to expect in this new guide to 2025 predictions and trends, here’s an A-Z list of some tech terms you may hear a lot more of in the coming year.
A is for AI and automation
Can talk of generative AI be avoided anymore? Unlikely. The big question, now that we’re well into the hype cycle, is: what’s the tangible, practical impact for my enterprise?
Here are a few ways we identified in our guide that AI is likely to impact businesses:
- Opening the door to more sophisticated cyberattacks and, ironically, playing a crucial role in defending against cyberthreats
- Automation in integration processes – from B2B integration to APIs and file transfer
- Revolutionizing API management and developer productivity
- Disrupting RPA solutions
- Autonomous accounting going mainstream
Read the full Looking Forward 2025 guide here.
B is for B2B integration
OK, B2B integration is hardly a new term, but there’s a lot shifting in the world of business-to-business integration, notably in and around the cloud.
From a marked acceleration of enterprises moving B2B integration workloads to the cloud in 2024, to the 360-degree pivot of an emerging trend for cloud repatriation, selecting B2B integration technologies that are versatile enough to offer portability options and multi-cloud support will be critical in 2025.
Then, of course, there’s the growing use of AI to automate nearly everything, and EDI processes won’t be left behind.
C is for containers
We’ve just brought up the big “C,” cloud, so let’s talk containerization technologies.
Containers are the latest virtualization technology where you can package up an application’s code and all its dependencies so it can run reliably in any environment.
2024 saw Axway’s B2Bi and MFT products evolve to a containerized architecture, offering tools and capabilities in a cloud-native deployment model to ensure customers can run at minimum or maximum capacity with peace of mind.
D is for data sovereignty
Data sovereignty is the idea that data should be subject to the laws and governance structures of the country in which it is located or collected, particularly regarding its storage, processing, and transmission.
Concerns over data privacy and sovereignty, particularly in Europe, says Axway CEO Roland Royer, are driving the development of decentralized and sovereign cloud solutions.
This also stands to impart more balance between cloud and on-premises or private cloud deployments, while giving enterprises more control over their data.
See also: Data governance in action: Axway’s leadership on privacy and security
E is for edge computing
Edge computing is a distributed computing paradigm that enables enterprises to process data closer to the source, reducing latency and allowing for real-time decision-making, particularly in sectors like manufacturing, healthcare, and IoT.
As edge computing expands, though, concerns around data governance are likely to intensify, says Ingo Muschenetz, Chief Architect, Head of Cloud Center of Excellence.
F is for federated API management
Federated API management is the practice of overseeing and controlling APIs via a common control plane across multiple environments, such as cloud, on-premises, and edge locations. It ensures consistent performance, security, and governance across today’s increasingly distributed systems.
As Mourad Jaakou, Amplify Platform VP & General Manager, notes, API governance and security must be improved, especially for large companies that have APIs spread through different technologies, geographies, and business units.
Critically, Axway’s 2024 Enterprise API Maturity Report found that enterprise decision-makers had very little visibility over these scattered APIs.
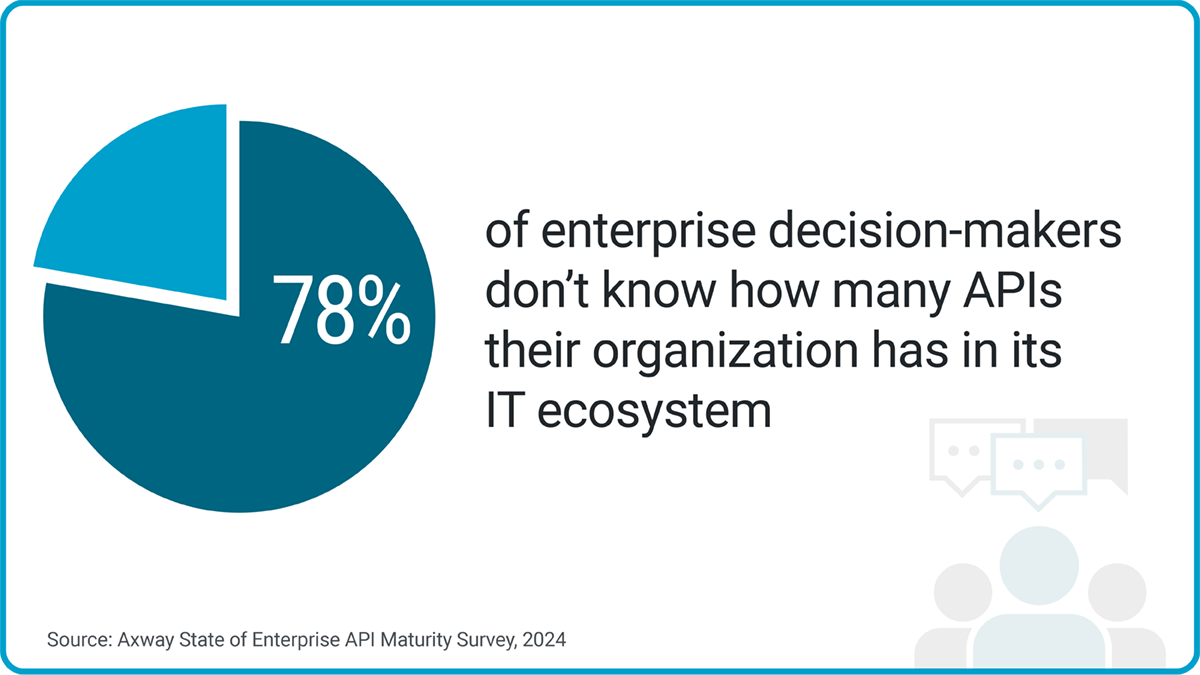
G is for multi-gateway
Staying on topic, one of the most impactful developments for API management in 2024 was the rise of multi-gateway management, says Sarah Guivarch, Senior Product & Solutions Marketing Manager for Amplify – and thus, a stronger need for federated API management platforms.
Discover Sarah’s thoughts on multi-gateway and more in the full Looking Forward 2025 guide here.
H is for “self-healing” software
What does it mean for software to heal itself?
Self-healing software refers to systems that can automatically detect, diagnose, and repair problems or errors during runtime without human intervention.
Self-healing managed file transfer, for example, includes features such as monitoring, analytics, and API-driven commands that contribute to automation – meaning the system can autonomously detect and resolve issues or errors that arise during file transfer processes.
I is for ITOps
ITOps isn’t a new concept, but its corollary, AIOps, is definitely a developing field:
- IT Operations (ITOps) refers to the processes and services administered by an organization’s IT staff to ensure the smooth functioning of their tech infrastructure, such as managing servers, networks, security, user support, and system maintenance.
- AIOps, explains Emmanuel Vergé, MFT Product Marketing Senior Director, is the practice of using big data, analytics, and machine learning to automate and improve ITOps.
Dive into Emmanuel’s vision of AIOps in the full Looking Forward 2025 guide here.
J is for jobs – the ones left vacant during talent shortages
Apologies for the stretch to fit the letter “J,” but the issue is real:
The global talent shortage, which spans nations states and industries, could reach 85 million workers by 2030, causing approximately $8.5 trillion in unrealized annual revenue, according to the World Economic Forum.
In most cases, it won’t be possible to have all these skills in-house, says Stass Pertsovskiy, Director of Product Marketing for Axway B2B – so a collaborative, open-system, and managed services approach will help address these challenges.
Meanwhile, Global Software Security Director Sandy Blackwell offers advice in our 2025 Looking Forward guide for identifying and nurturing the precious talent you may already have.
K is for Kafka
Apache Kafka is a distributed event streaming platform that’s specifically designed to handle real-time data. It simplifies the process of managing data flow and ensures efficient delivery while maintaining high performance.
Real-time data is in high demand: over the last years, we’ve noted a rapid increase in Axway customers leveraging Kafka, both alongside and in connection with our solutions.
Read more: What is Apache Kafka? Understanding Enterprise Data Streaming
L is for Legacy
By definition, legacy IT isn’t new – it’s on borrowed time. But there’s no question that time is starting to run out. “Legacy MFT solutions might not look broken, but they are,” writes Shari Lava, Senior Director, AI and Automation at IDC.
And the emergence of quantum computing is likely going to force every enterprise software to adhere to new security standards, adds Astrid Fischer, Principal Product Manager, MFT at Axway.
M is for machine learning
Machine learning is a subset of artificial intelligence that enables computer systems to automatically learn and improve from experience by identifying patterns in data, without being explicitly programmed for each specific task.
Alongside AI, it’s been increasingly embedded into integration platforms to:
- automate tasks like mapping, error detection, and data flow optimization
- enhance predictive analytics
- improve personalized customer experiences
- and much more.
One concrete example: ML can help reduce accounting errors, which could improve the accuracy of financial statements.
N is for no-code (or low-code) platforms
Low-code/no-code platforms are development environments that allow users to create applications through visual interfaces and drag-and-drop components rather than traditional programming, meaning that end users or “citizen developers” can produce applications that are more closely tailored to their needs.
It certainly doesn’t mean coding skills will just evaporate – especially comes to the complex needs of large enterprises, says Stass Pertsovskiy. This complexity means that experts will still be required to write custom code, configure environments, and design flows to address these specific needs.
On the other hand, these platforms are certainly shifting the way we work. Learn how in the full Looking Forward 2025 guide here.
O is for open banking
2024 was a big year for open banking – defined as enabling third-party software providers and banks to build new, customer-centric financial applications and services using APIs. The CFPB finally gave teeth to Section 1033 of the Dodd-Frank Act in October 2024, which gives consumers the right to access and share their financial data – effectively mandating open banking in the USA.
Latest updates: Section 1033 of the Dodd-Frank Act became law in January 2025, but recent White House actions against the CFPB have led to some uncertainty over the agency’s future. Get the facts here.
2025 will be crucial in transforming North American financial services for the long term – and Axway is off to a strong start already. Mourad Jaakou adds that it’s important to look to the opportunity beyond just compliance.
“With the help of core banking providers developing turnkey open banking solutions, smaller institutions could gain a “first mover” advantage, with lower risk and potentially faster time to market.”
P is for privacy
Is there such a thing as privacy anymore in our age of oversharing and fuzzy online borders? If regulations such as GDPR or yet-unnamed future data privacy laws are to play a role in shaping software development priorities, then yes.
Already, we are seeing a big push for greater data governance integration, says MFT & B2B Solutions Architect Jose Villanueva.
And the global expansion of privacy regulations is expected to prompt enterprises to prioritize data protection, security, and regulatory compliance in their software development processes, says Georgiana Weaver, Senior Product Manager, Amplify Enterprise Marketplace.
Q is for “Q-Day” (and quantum computing)
Q-Day refers to the hypothetical future day when quantum computers become powerful enough to break classical cryptographic systems, such as RSA and ECC, which secure most of today’s internet communications.
It would represent a critical moment for cybersecurity, since encrypted data could become vulnerable to decryption by quantum algorithms like Shor’s algorithm.
Post-quantum cryptography (PQC – i.e. the development of and transitioning to quantum-resistant cryptographic methods) is probably not being taken seriously enough, argues Sandy Blackwell.
Quantum Computing Could Break MFT Encryption – What To Know Now
R is for ransomware
Ransomware isn’t new, but what may be surprising is that despite widespread awareness of recent breaches, it continues to grow. One cybersecurity conglomerate noted a 24% quarter-over-quarter increase in ransomware attacks targeting consumers during Q2/2024.
Then, there’s the shift in ransomware tactics, where hackers target businesses’ backend systems. Discover how they are evolving in the full Looking Forward 2025 guide.
S is for standards
2025 will be a big year for API standardization in the banking industry, with the Financial Data Exchange (FDX) this month becoming the first recognized standard setting body under the Consumer Financial Protection Bureau (CFPB)’s Personal Financial Data Rights rule.
Regardless of regulatory pressures, the success of an open approach to financial services is rooted in a common language that allows all players in an ecosystem to participate.
Last year also saw the emergence of the Arazzo Specification, notes Brian Otten, VP Digital Transformation Catalysts. It’s a new community-driven technical API standard that is complimentary to OpenAPI, aimed at defining language-agnostic workflows and dependencies between multiple API calls.
Meanwhile, voluntary participation in France’s B2B e-invoicing standard starts this year, with plans to mandate it by September 2026.
T is for 2025’s threat landscape
Cyberthreats are not only becoming more sophisticated, but the pace of attacks has been accelerated, says Sandy Blackwell – particularly when you factor in AI, which expands the attack surface, and which attackers also have access to.
Traceable’s 2025 Global State of API Security Report found that 57% of organizations experienced at least one data breach caused by an API exploitation in the past two years, underscoring the ongoing risk that APIs present – especially the unknown, unmanaged ones.
Zombie API apocalypse: How to Protect Your Systems and Survive
U is for UI/UX
Adaptive user experiences mean that it is no longer static for every user, but will adapt to user needs, presenting only the most relevant information and features. Any repeatable tasks are minimized or simplified as much as possible and supported by natural language prompts.
This may be one of the reasons Georgiana Weaver predicts that individuals skilled in UI/UX design will be in high demand in 2025.
V is for verification ramp-up
At this point, it’s clear that regulations around AI security and access to data will impact software development. In the context of IT and digital credentials, “verification” is the process of confirming the authenticity, validity, and integrity of a digital credential by:
- Validating the issuer’s digital signature
- Checking the credential’s cryptographic proof
- Ensuring the credential hasn’t been tampered with or revoked
- Confirming the credential matches the claimed identity or attributes
Verification helps prevent fraud by establishing trust through cryptographic and digital authentication mechanisms, allowing rapid and secure validation of credentials across digital platforms.
And as Marcus Chang, Principal Product Manager, Traceability and Regulatory Compliance notes, we may see an increase in calls for usage of verifiable digital credentials to combat fraud.
W is for warning: “don’t be complacent under perceived normalcy”
In some organizations, Sandy Blackwell explains, enterprise leaders may know of threats or risks without always understanding the impacts if they are exploited.
“When we see breaches that have worldwide impacts, everyone wants to be able to say their organization is looking at those risks. None of the largest breaches or incidents have included anything that a good security team isn’t already sharing with their management.
The OWASP top 10 hasn’t changed much in many years, and zero days happen without warning. The same problems exist and are still being exploited; those that haven’t happened yet, may surface tomorrow,” concludes Sandy.
See also: Unsecured Cloud File Transfers: Dangers & Costs
X is for… the platform formerly known as Twitter
You’re still calling it Twitter in your head, too. Right? But it would seem the new name is here to stay.
People using the platform, though, appear not to be staying: Mashable reports that X is projected to lose millions of users in 2025.
Y is for YOLO
OK, we admittedly had to dig pretty deep for this one, but here’s an interesting AI-related term: YOLO.
Not the carefree lifestyle philosophy – in this case, YOLO stands for You only look once, an object detection algorithm that processes images in a single pass to identify and locate multiple objects simultaneously.
It’s widely popular because it offers an excellent balance of speed and accuracy while being relatively straightforward to implement, making it ideal for real-time applications like autonomous vehicles or video surveillance.
The A-Z of AI: 30 terms you need to understand artificial intelligence
Z is for zero trust security
Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a network, regardless of whether they’re inside or outside the organization’s network perimeter.
Traditionally, security was focused on building a bigger “wall,” but nowadays it needs to extend past the exterior perimeter, with a focus on continuous authentication at every level.
See also: Zero Trust security model: A modern approach to MFT
Roland Royer points out that growing cyberthreat complexity is likely to accelerate the adoption of Zero Trust architectures across enterprises, where strict identity verification across devices and users will be the new normal.
It’s also one reason professionals skilled in Zero Trust architecture, threat detection, and incident response should be in high demand this year.
Dive into Looking Forward 2025 for more in-depth, strategic insights
We hope this was a helpful – or at least, entertaining – guide to some of the buzzy tech terms of the day. More than that, the full guide is designed as a launchpad to deeper understanding of the current industry’s state.
We said it last year: busy IT decision-makers don’t need more buzzwords. You’re looking for concrete advice as you shape your business strategy. This year’s 2025 predictions guide is packed with actionable insights, and we can’t wait for you to discover it.
Download the Guide: Looking Forward 2025 here.

