Ask most people what the biggest threat in IT is, and they’ll say “AI” — hailed for productivity and feared for job loss. Yet the more consequential risk may be waiting offstage. Quantum computing, a field overshadowed by the AI frenzy, has the power to render current cryptography algorithms useless and, as a result, turn everyday electronic secure communications into a free-for-all.
What is quantum computing?
Let’s take a step back and explain what quantum computing is.
Today’s computing – now called classical computing due to the impending rise of quantum – uses a unit known as binary to represent data. These 1s and 0s are combined into strings to produce numbers which can then be mathematically computed by processor chips at rapid speeds, resulting in what we see on our screens, the performance of calculations, and electronic communication.
Quantum computing makes use of qubits. Qubits can be in many states at once beyond the traditional 1 and 0, and can be linked (known as entanglement) and even interfere with one another. It’s a difficult one to wrap your head around, but what is important to know is that quantum computing isn’t necessarily faster than classical computing, as many misconceive it to be. It is instead extremely good at preparing all possible answers to a question, and then iteratively amplifying probable correct answers until a single and correct outcome is observed.
See also: Axway’s Looking Forward 2025 Guide
Why is quantum computing a threat?
We have established that, broadly speaking, quantum computing isn’t faster than classical computing and therefore isn’t suited to everyday IT tasks such as reading this blog or simple arithmetic. In other words, quantum computing as it exists today isn’t going to replace your laptop or mobile device.
Where quantum computing does have an advantage is in scenarios where the use of iteration to determine probability, discarding incorrect answers until a final correct and true answer has been determined.
Here are some examples:
- Search and optimization of unstructured data and information can be sped up with the use of quantum computing.
- Scientific simulations can be run using quantum computing, with desirable and correct outcomes being determined at speed. Consider the use of this in the R&D of new drugs and medicines.
- Asymmetric cryptography, such as RSA, DH, and ECC, relies on math problems that a large, fault-tolerant quantum computer could solve efficiently with Shor’s algorithm.
In relation to MFT and IT in general, it is that last bullet point which should have made the penny drop.
The threat of quantum computing is that it could render much of the asymmetric encryption used prolifically today useless.
How long do we have until quantum computers are available?
However, it isn’t time to sound the alarm just yet. While the threat is real, quantum computers are not quite within the realm of general availability today, except for research – and those are still experimental and error-prone.
Current estimates by IBM are that useful and fault-tolerant systems will plausibly be available around the late 2020s and early 2030s.
Despite this, there is growing evidence that state-sponsored actors and hackers are stealing and storing huge amounts of encrypted data today, so that they can decrypt and make use of it when quantum computing or other techniques become available.
Known as quantum harvesting or sometimes “harvest now, decrypt later”, encrypted data is being stored for a time when it can be broken. Blueprints for defense equipment, identification documentation, and intelligence gathered by government departments are all examples of data being low risk when lost in an encrypted format, to being high risk when the means to read them become available.
Suddenly, company policies to encrypt removable storage so that they can shrug their shoulders when lost are now becoming as problematic as if they were not encrypted at all.
How does this apply to MFT?
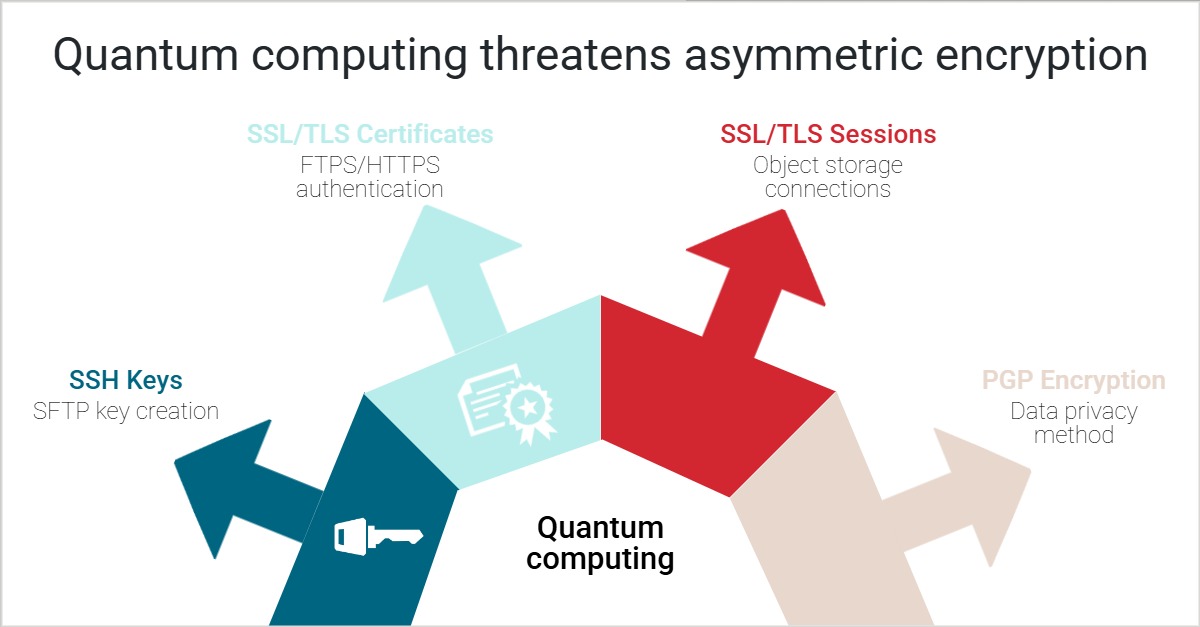
In relation to the threat of quantum computing, it is the use of today’s asymmetric encryption cryptography which presents the greatest risk.
Uses of asymmetric encryption in MFT include:
- The creation and use of SSH keys in SFTP.
- The creation and use of SSL/TLS certificates for FTPS and HTTPS authentication.
- The setup of SSL/TLS sessions over SSL, for example, connecting to object storage solutions such as AWS S3 and Azure blobs, or server-to-agent / peer-to-peer connections as part of the MFT architecture.
- PGP encryption.
It is critical to understand that quantum computing is more of a direct threat to asymmetric encryption than it is to symmetrical encryption, due to Shor’s algorithm and the exponential advantage it has when used in quantum computing. Commonly used symmetric encryption algorithms, such as AES and RC6, are less vulnerable and can be improved by simply increasing the key length.
But… as asymmetric encryption is usually employed as a mechanism to securely exchange symmetric keys between two parties (symmetric encryption is much faster than asymmetric), it could leave symmetric keys vulnerable to breached exchange processes.
Worried yet?
How can we face down this threat?
All is not lost.
In 2016, NIST began standardizing the future of PQC (post-quantum cryptography) by launching a competition to find encryption algorithms that are quantum-resistant.
Of the ninety-six submissions, NIST has approved and created three PQC standards as of August 2024 – FIPS 203, FIPS 204, and FIPS 205 — with FIPS 206 in draft and a fifth standard expected in 2027.
- FIPS 203: a general encryption standard based on the CRYSTALS-Kyber algorithm, renamed as ML-KEM (module-lattice-based key-encapsulation mechanism).
- FIPS 204: the primary standard for protecting digital signatures. Making use of the CRYSTALS-Dilithium algorithm, renamed to ML-DSA (module-lattice-based digital signature algorithm).
- FIPS 205: also designed for digital signatures, but using the SPINCS+ algorithm, now renamed to SLH-DSA (stateless hash-based digital signature algorithm).
- FIPS 206: a draft standard using FALCON, a lattice-based digital signature algorithm.
- Fifth standard: using Hamming Quasi-Cyclic as a backup for ML-KEM in FIPS 203 in the event weaknesses are found in the future.
These encryption algorithms, widely known as PQC algorithms, are slowly making their way into IT solutions and should be used where possible to head off further quantum harvesting activities.
What are the positives of quantum computing?
It is easy to get carried away with the negatives of quantum computing, but it is overtly a positive development that has the potential to propel many industries, such as health and pharmaceuticals, into new golden ages.
Today, AI is already assisting in the creation of new treatments, discovering new antibiotics, and assisting in genome sequencing of viruses. Being able to use quantum computing techniques to complement these activities through modelling, discovery of personalized treatments, and molecular analysis could be as impactful on the future health of humans as the works of Louis Pasteur, Edward Jenning, or Alexander Fleming.
A little closer to home, there is intense interest in how AI could be empowered by quantum computing.
How is Axway planning for the future of quantum computing?
The core tenets of Axway MFT are security, reliability, and scalability – three words which permeate everything we do.
With security in mind, the Axway product team has been researching and following the development of PQC with keen interest. As standardized PQC encryption and key generation algorithms become available in the libraries which are used by our solutions, our customers will begin to see these released to them by way of product releases.
Frequently Asked Questions
Is quantum computing faster than classical computing?
Yes, however, the benefit of their use depends on the use case. Quantum computing is best at quantum calculations, where the best solution to a problem can be determined by discovering all possible solutions and iteratively promoting and excluding solutions based on their probability until the best solution is found.
Unlike binary in classical computing, which can have a state of either 1 or 0, qubits can exist in either or both states until measured, allowing them to represent a wider range of possibilities.
Can quantum computing techniques make managed file transfer solutions vulnerable?
In short, yes. Wherever asymmetric encryption is used, there is a vulnerability to quantum computing. Asymmetric encryption is widely used in MFT for securing communication channels, data encryption, and authentication.
What is the risk of quantum computing to managed file transfer today?
Today, quantum computers are not in widespread use, and so the immediate threat to asymmetric processes such as SSL/TLS, SSH keys, and PGP is limited. However, it is well documented that malicious actors are collecting and harvesting encrypted data, keys, and certificates for use in future when they can use quantum computers against them. Therefore, it is imperative that encryption standards which are resistant to quantum computing are used as soon as they become available.
Are PQC algorithms available in Axway MFT today?
Today, we haven’t approved or released any PQC algorithms into our MFT solutions, however, our product teams are working on it. There are several dependent libraries which need to be updated and tested before this is possible.
As well as having a focus on security, Axway MFT is used by some of the world’s largest organizations and most recognizable brands, and therefore we acknowledge our responsibility to ensure we provide reliable solutions which have been suitably tested against our high standards.


