The largest attack vector in most organizations is unmanaged, unsecured APIs. The ones you do not know about today. The ones not showing up in your inventory of API assets.
Whether you call them zombies, shadow APIs, or legacy assets, the race is on for you to discover and remediate these before the hackers do.
Today, Amplify offers a new tool in your battle against the lost APIs.
Unmanaged APIs are your biggest security risk
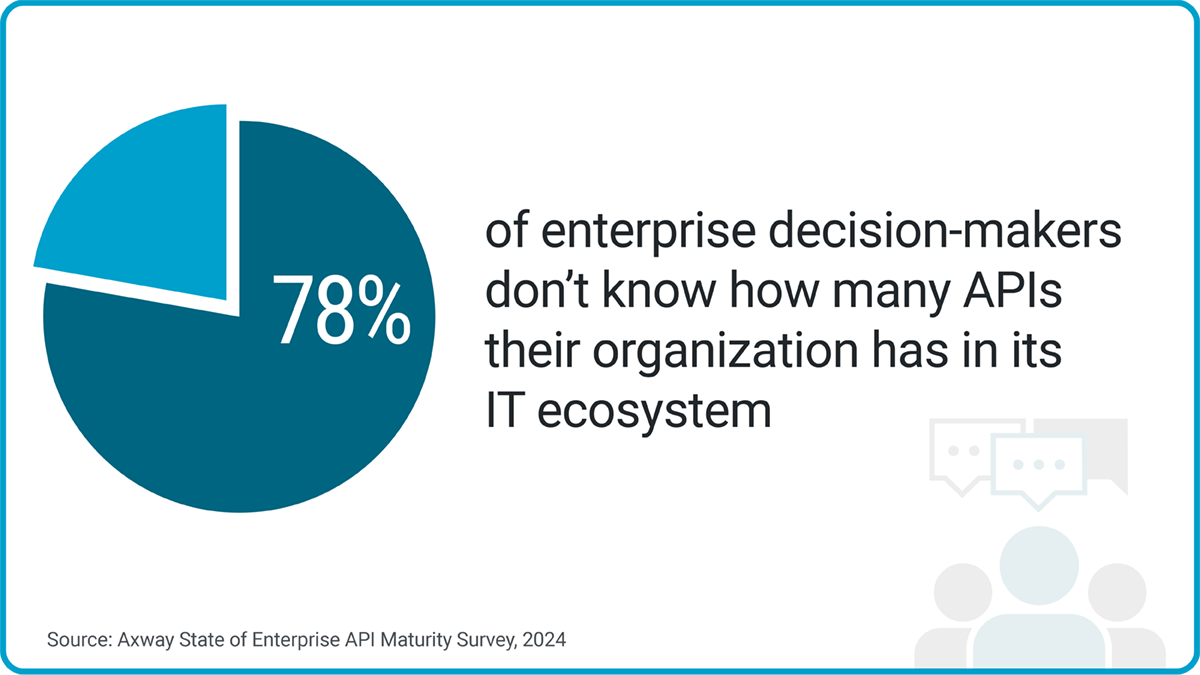
Amid sprawling API growth, enterprises have a visibility problem. A recent survey we conducted finds that more than three-quarters (78%) of enterprise decision-makers don’t even know how many APIs they have.
In a Traceable survey of financial services institutions, a staggering 73% of respondents report that malicious bots are a moderate to critical threat to their API security.
This isn’t something you can afford to overlook. The average cost of an API security breach today is $6.1 million, including the damage to an organization’s reputation. That’s set to nearly double by 2030.
How can enterprises stop the drain of this expensive security risk? There are several best practices to stop producing lost APIs. Let’s highlight the ones leading organizations are implementing.
But first, a few definitions may be helpful.
Understanding lost APIs
Shadow APIs, Zombie APIs, and Legacy APIs are slightly different concepts, but they all represent outdated or unauthorized elements within an organization’s API ecosystem. Here’s a quick overview to better understand these lost APIs:
A zombie API is an API that is outdated, no longer supported, or has been deprecated but is still in use by some systems or applications. It’s called “zombie” because, like a zombie in popular culture, it’s technically dead but still somehow wandering around causing trouble.
You may have also heard the term shadow APIs. The main difference with zombie APIs is that shadow APIs are actively being used – they’re just not well-known, cataloged, or managed by the enterprise. These APIs are often developed by individual teams or departments to address specific needs but may lack documentation, security measures, or proper integration with existing systems.
Zombie APIs are typically deprecated but haven’t properly been put to rest.
Legacy APIs, meanwhile, are APIs that have been officially deprecated or superseded by newer versions or alternative solutions – but they are still in use by some applications or systems.
All these lost APIs might lack updates, bug fixes, or security patches, posing potential risks to systems that continue to rely on them. They can also create compatibility issues and hinder the development of newer, more efficient solutions.

Controlling your API landscape requires a two-pronged approach: discovery and mitigation.
Discovery identifies all your APIs, both managed and unmanaged, providing a crucial understanding of your current state. Mitigation equips you with the tools and processes to take action, bringing those APIs under governance.
We’ll explore the intricacies of API discovery later, but let’s first examine the organizational structure you need to establish for effective API management.
Create a common API lifecycle practice
First, you need to get a process in place and define a lifecycle that can be adopted and enforced within your organization. This involves defining well documented series of stages that an API progress through.
Here is a common set:
- Define
- Design
- Develop
- Test
- Secure
- Deploy
- Distribute
- Observe/Monitor
- Version
- Retire
This gives structure and tracking to where your APIs are at any given time and helps ensure no API is left behind.
API Security Tools and Best Practices
Axway’s 2024 State of Enterprise API Maturity report highlights some of the ways that insufficient visibility over the API stack can expose an organization to monitoring and governance issues.
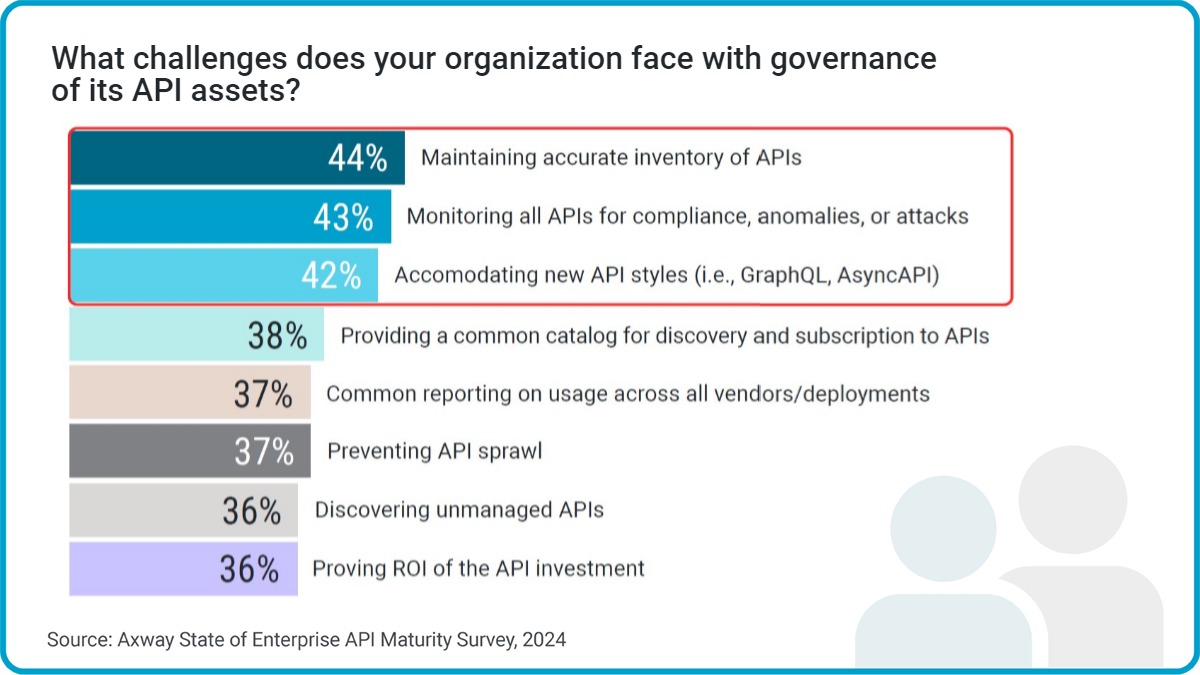
IT decision-makers are especially concerned about the lack of accurate API inventory (46% vs. 42% for business leaders), but both have some awareness that unknown risks lurk.
Other vulnerabilities enterprises face include:
- different security configurations for internal vs. external APIs (46%)
- unrestricted resource consumption (i.e., DoS attacks — 43%)
- inadequate access and authorization controls (41%)
- lack of common security policy enforcement for APIs (37%)
Without central governance, enterprises find themselves relying on the capacity of their internal dev teams. And remember, that’s just for the APIs they know about and are managing.
Create one registry for all your API assets
There needs to be one place where all your APIs can be governed. This is the master catalog or registry of assets — an API marketplace.
You might decide not to advertise them, but you need to track and manage them. Because it provides you a federated API management foundation, Amplify Engage gives you this one place.
Discovery of assets is automated by lightweight agents that sit alongside your gateways, platforms, and repositories and discover all API assets. You can then decide which to productize and publish to a specific audience.
This provides your developers with one place to discover, subscribe to and track usage for all APIs, regardless of what team built them, what vendor hosts them, or what security policies are in effect.
See also: Top seven reasons your API developer portal is failing
Check against your security policy
Amplify also enables you to check discovered APIs against your security policies (you do have security policies… right?) where they will be graded and provide explanations as to what needs to be corrected for a higher grade.
This capability is known as linting, and it automates the identification of problems without manual intervention. Amplify uses the open source Spectral linting capabilities provided by Stoplight to drive this service.
See also: Hands-on with Spectral: Using API linting for better API design and API governance
Automate the API deployment process
Don’t depend on API developers alone for security (one of the leading causes of zombies in the first place). Automate as much of the process as possible.
With CI/CD pipelines, you can automate the discovery, cataloging, and linting checking of your APIs as a part of the standard deployment process.
This can be accomplished regardless of whether you are using Amplify gateways or cloud gateways like AWS and Azure. This helps ensure you stop the creation of new zombie APIs.
Find all your APIs
74% of decision-makers report that more than 20% of their organization’s APIs are unmanaged, according to our State of Enterprise API Maturity survey. There’s a good chance your enterprise falls somewhere in that range as well.
By definition, you do not know where the lost APIs are in your organization. They fall outside the scope of your defined processes and tools. To discover them, you must go beyond “standard” and start scanning your infrastructure and watch occurring traffic in an attempt to locate them.
There are many tools to choose from, but they all face the same problem: how to differentiate the good traffic from bad traffic, and how do you bring them into the fold?
Security scanning tools use algorithms to identify common patterns like Denial Of Service or brute force attacks and stop them. They are good at capturing and logging all API activity (GET’s, PUT’s, etc.).
The problem with lost APIs is that they behave exactly the same way as valid, managed APIs to many of these scanning tools. This is where Axway can help mend that gap.
Amplify Engage offers a governance plane for all APIs across your organization, providing a single source of truth regarding your digital assets. They can be deployed directly on top of gateways or from central places within network segments that allow access to gateways or systems that communicate via APIs.
Learn more about Amplify Agents and how they enable federated API management.
Amplify now also provides various prebuilt agents to incorporate the results of API security solutions, scanning real-time API traffic across your organization. The results of these are continuously compared against Amplify’s known list of all managed API assets and endpoints, to understand the scope of the unmanaged or lost APIs at any time – and allowing you to remediate swiftly.
All APIs – Managed APIs = Lost (Unmanaged) APIs
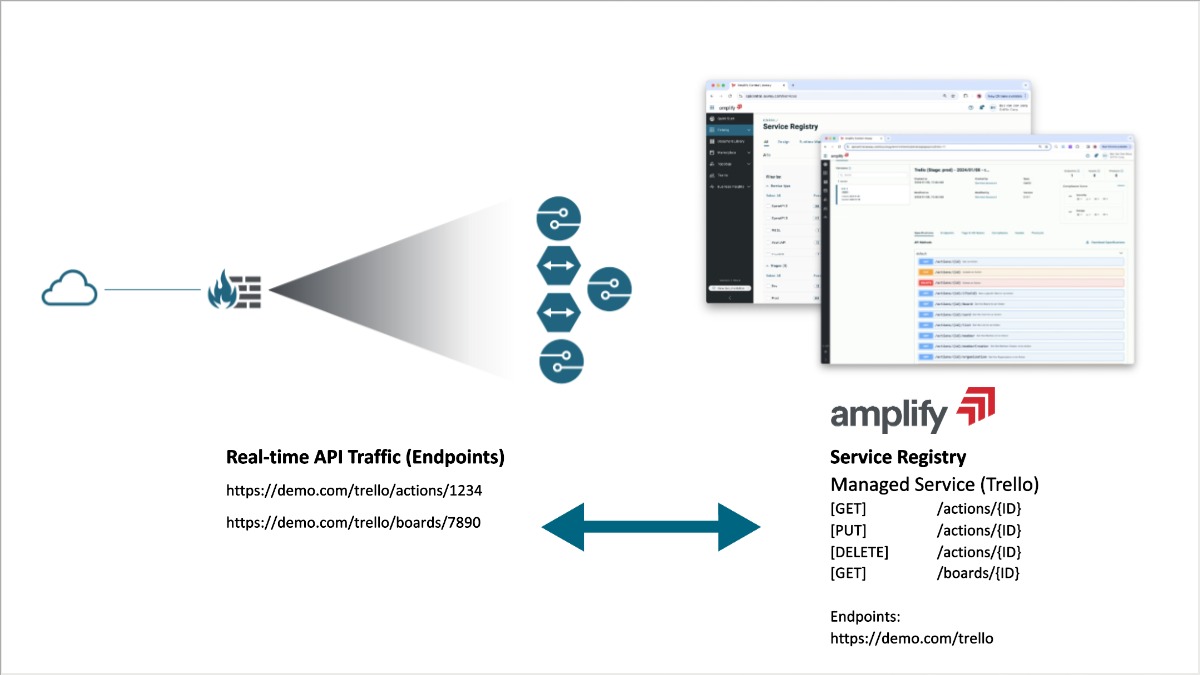
This makes it possible to combine, enrich, correlate, query, and visualize all your APIs in one place, and captures real-time traffic to search, visualize, alert and report on operational and security problems.
Amplify provides the single repository of all API assets and automatic discovery of APIs, which enables you to:
- Map your runtime traffic against your managed API infrastructure and identify outliers (unmanaged APIs)
- Prioritize APIs for remediation (based on traffic and risk assessment)
- Continuously monitor, identify, and repeat
No API left behind: how to remediate lost APIs
Once you find the zombies, shadow, or legacy APIs, you need to prioritize for remediation.
- Target the ones that offer the highest risk because of the information they expose, or the volume of traffic they are driving
- Find the team who created and/or are hosting the API and educate them to the risk and your security policy to deal with it
- Decide whether it needs to be kept or killed
- If kept, secure the API. This typically involves placing it behind an API gateway with encryption, authentication, and authorization (Amplify can provide this gateway if needed).
- Contact and educate the APIs consumers and transfer them to the new managed APIs
- Deprecate and remove the unmanaged API
Next up is to integrate it with Amplify’s multi-step security protection.
Automate and repeat
Regardless of how good your tools, processes, and policies are, there will still be teams that create the one-off API that is “just needed for a deadline” or for testing that becomes a legacy API.
You must automate the process to find them and then make the decisions of how to remediate. Only through automation and vigilance can you keep on top of the shadow API problem.
As hackers become more sophisticated, so must your tools and processes advance. Amplify will continue to bring new capabilities to assist in the battle against hackers and zombies.
Death to zombie APIs!

