System security isn’t just a checkbox. It’s a culture, mindset, and strategy. The best security system that helps you avoid financial and reputational losses is the one that is resilient, not reactive.
In today’s digitally interconnected world, even sophisticated teams can get hit hard by security breaches. Businesses lose millions of dollars because of exposed API keys, ransomware, and mishandling sensitive data flows.
How do you build a system that stops data breaches before they start?
Axway’s approach to system security rests on four main pillars. We covered them in detail in a recent webinar, and I’d like to break them down in this article.
Assume a breach, verify everything, minimize exposure
Never trust, always verify. Your layered security system must assume that every request is potentially hostile.
Zero Trust architecture goes further than just identity checks and firewalls. It’s not about making things harder, but controlling processes in an intelligent manner.
Answer these five questions to manage your Zero Trust infrastructure:
- Who gets access, and is it least privilege access only?
- Which devices get access, and do you verify them at every checkpoint?
- Where in the network is the connection happening?
- What is being accessed: apps, APIs, or files?
- Why is it needed, and do you secure your data with encryption, tokenization, or access control?
You don’t need to have five different tools to answer these five questions. Axway provides a unified security and governance layer in our Axway Managed Cloud.
Out of the box, Managed Cloud customers get a single solution that enables zero-trust architecture, giving you peace of mind to focus on your business.
Discover. Validate. Protect
92% of organizations use APIs to connect with their partners, customers, and internal services. Only a fraction of them can detect and monitor their API inventory and usage. In fact, almost half of all organizations cite API sprawl as their top security concern.
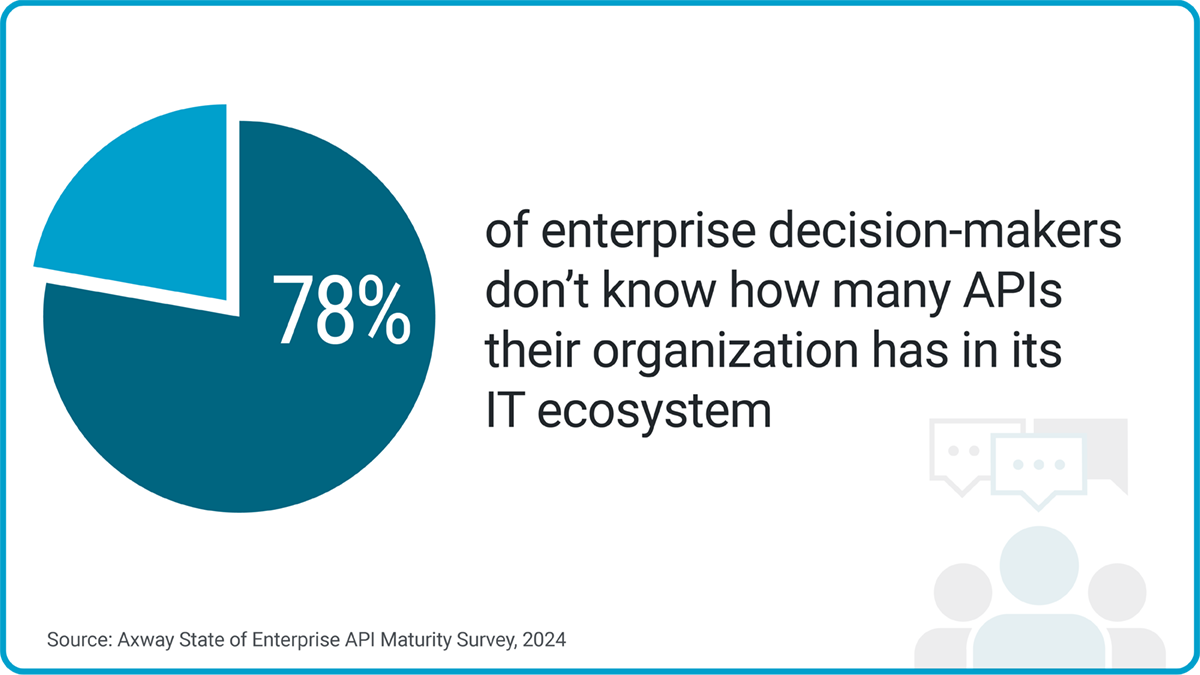
Threats result from APIs you can’t see and manage – these are zombie APIs, shadow APIs, and legacy APIs.
Zombie, shadow, and legacy APIs are active or deprecated systems that continue to work secretly and unmonitored, providing unlocked and unattended doors into your systems. They’re a security breach waiting to happen.
We describe each type of these unmanaged APIs in this blog.
These risks are easy to eliminate. Discover, validate, and protect your systems in one platform: Axway Amplify.
Axway’s API management solution helps companies secure their API infrastructure with three processes. Axway Amplify crawls your system and identifies all active APIs across different environments.
Once APIs are discovered, Amplify validates them and helps you discard unwanted APIs or add centralized policies like OAuth 2.0, Schema Validation, rate limiting, and more.
When APIs are discovered and validated, Amplify protects your system with real-time tokenization, IP limiting, volume anomaly detection, and usage threshold. Amplify provides full visibility into who uses your APIs, when, and how.
Context, patterns, response time
Security breaches don’t always happen instantaneously. The worst intrusions can go undetected for weeks or even months.
The average time a breach goes unnoticed is a whopping 204 days – and it takes an additional 77 days to contain. That is more than 9 months of financial and reputational losses for your business.
Threat detection is work done smarter, not harder. Think beyond simple alerts. Think context, patterns, and response time.
Start by identifying your baseline behavior. For APIs, that is defining who accesses what, when, and how often. For MFT, identify the standard rate of file transfer by each partner. Establishing the baseline is an important step that will help you track anomalies.
When you know the normal rates of usage, it is easier to identify spikes in data volume access from unusual places or repeated failed authentication attempts. Unified anomaly detection enables correlation tracking: when several unusual signals converge, you may have an active security breach.
Learn how Ciena, a global leader in networking systems, services, and software, reached 100 percent availability of its MFT system with no security incidents to date using Axway SecureTransport.
You’re not alone
Your security is only as strong as your weakest integration.
Just as it is important to protect your own digital environment, it is equally important to protect your entire digital supply chain.
All it takes for a security breach to happen is one unlocked door. This door often looks like a trusted third-party integration.
Take the following precautions to help mitigate and eliminate these threats:
- Continuously monitor partner integrations for suspicious activity, like you monitor internal users.
- Ask your partners for a software bill of materials and API visibility to learn more about your integrations.
- Dashboards are useful tools to monitor traffic, so you can learn who moves data, where, and why.
- The most dangerous blind spot is third-party files and API drops – that’s where secure files have the least visibility.
No one silver bullet can safeguard your digital systems from vulnerabilities. But this security strategy will help defend your most critical data flows.
With your own systems or partner integrations, leaning on these four pillars will help you build a security system that is not reactive but resilient to attacks.
Axway can help you gain visibility into external connections, tackle API chaos, and mitigate third-party risks without slowing down your business.
Learn how Axway’s API, MFT, and B2B solutions help Germany’s federal labor agency defeat 5 million cyber threats daily.

