OAuth is a powerful authorization framework that has become the backbone of secure API access. It’s a cornerstone for security in the web world, but its complexity can be daunting.
Today, we’re breaking down OAuth into its fundamental components, focusing on choosing the right grant type, aided by scenarios and sequence diagrams.
Understanding OAuth grant types
OAuth defines several “grant types” — methods through which an application can get permission to access resources. Each grant type is designed for different use cases, balancing security concerns with practical implementation needs.
See also: How to easily secure your APIs with API keys and OAuth
1. Authorization code grant
Ideal for: Applications needing to perform actions on behalf of a user
Scenario: Imagine a web-based email service that needs to access your calendar events to create appointments. Using the authorization code grant, the service can request access without ever handling your calendar login credentials. Instead, it receives an authorization code that it can exchange for an access token.
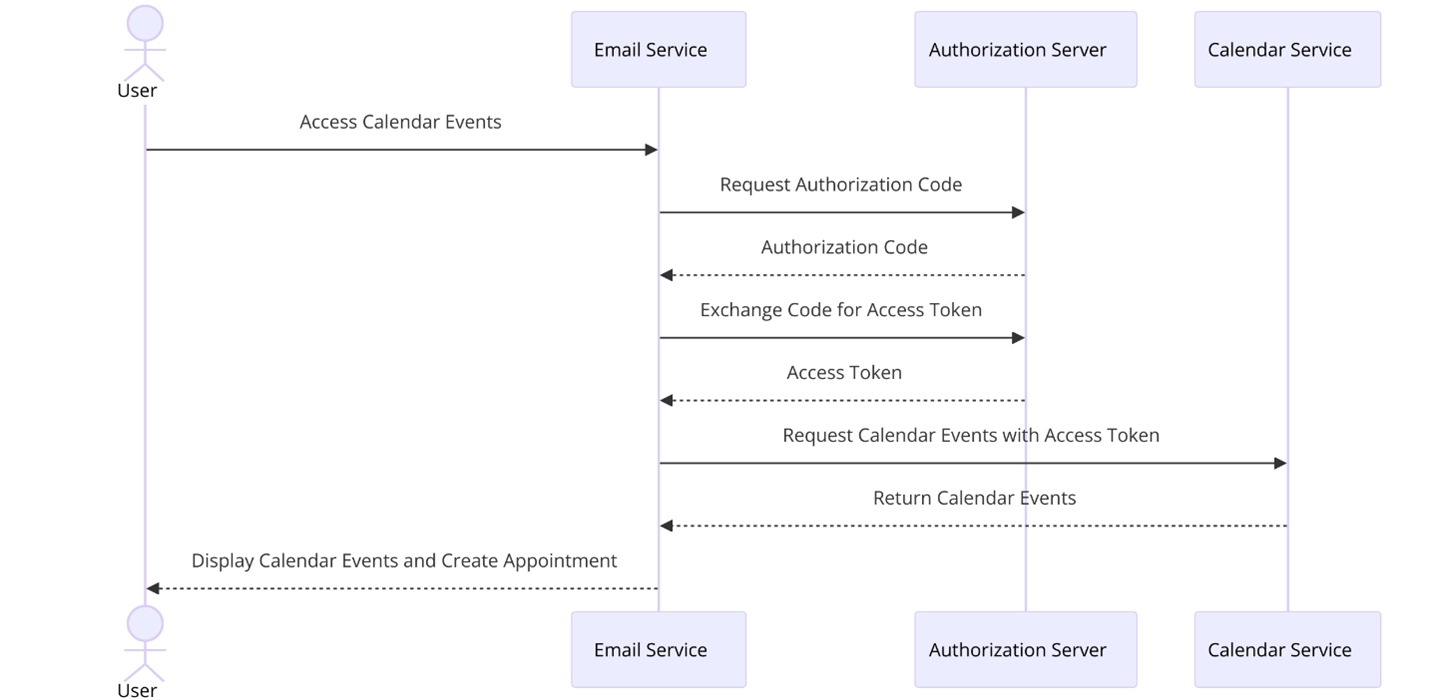
Sequence diagram illustrating the authorization code grant OAuth flow for a web-based email service accessing calendar events
For the authorization code grant, the components required are:
- Client ID and client secret: These credentials identify and authenticate the client application.
- Authorization server: Manages user authentication and provides an authorization code to the client after the user logs in.
- Authorization code: A short-lived code that the client application exchanges for an access token.
- Redirect URI: The URI to which the authorization server sends the authorization code after the user is authenticated.
- Access token: The token that the client uses to access protected resources once the authorization code is exchanged.
Technical setup: The client application redirects the user to the authorization server for login. Once the user is authenticated, the server sends an authorization code to the specified redirect URI. The client then exchanges this code, along with its client ID and client secret, for an access token.
This flow ensures that sensitive information like the user’s credentials and access token are handled securely, typically by server-side components rather than the client.
Why it works: It provides enhanced security by handling user authentication directly with the service that hosts the user data, thus minimizing the exposure of user credentials.
Note: This method is secure as the tokens are handled by the server, away from the client.
2. Implicit grant
Ideal for: Client-side applications where the application’s authenticity cannot be easily verified.
Scenario: A browser-based game wants to post scores to your social media. It uses the implicit grant to obtain tokens directly without an intermediate authorization code step, simplifying the flow at the expense of exposing tokens to the client environment.
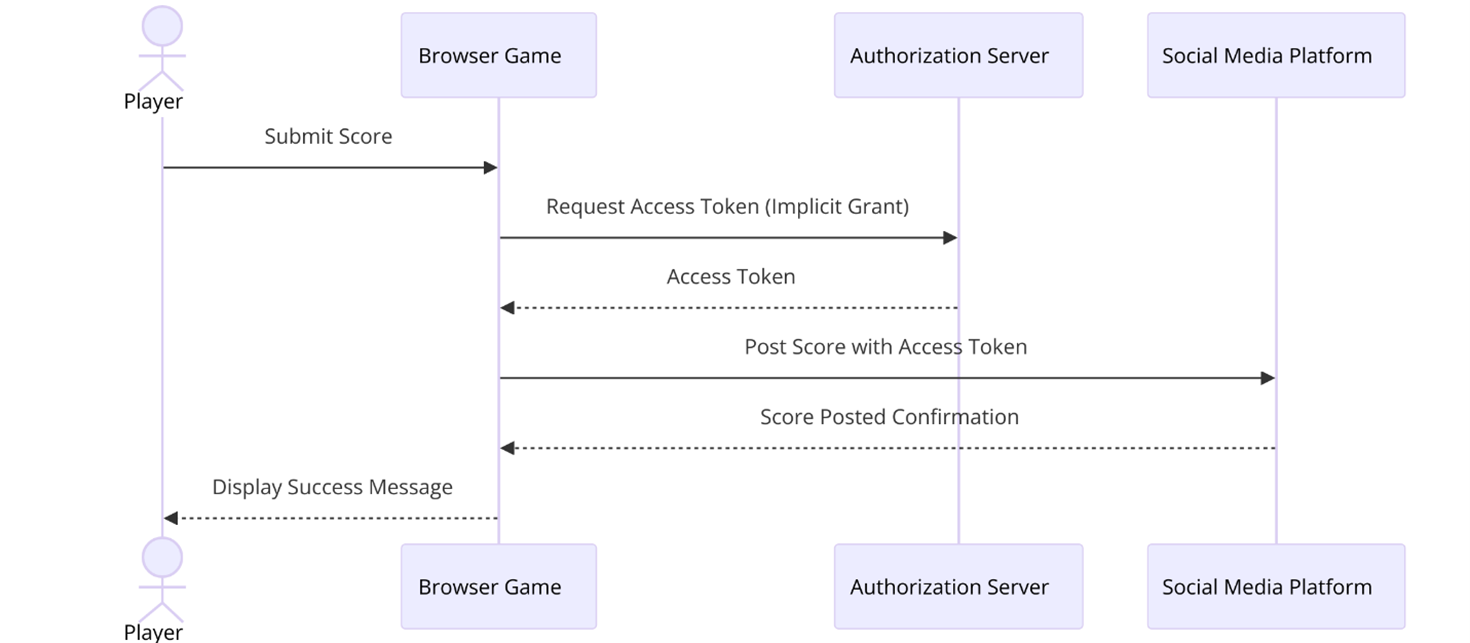
Sequence diagram illustrating the implicit grant OAuth flow for a browser-based game posting scores to social media
For implicit grant, the following components are necessary:
- Client ID: Uniquely identifies the client application (typically a single-page web or mobile app).
- Authorization server: This server handles the user’s authentication and immediately issues an access token without an intermediate authorization code step.
- Redirect URI: The URL to which the authorization server sends the access token once the user is authenticated.
- Access token: This token is sent directly to the client application and used to access protected resources.
Technical setup: The client application (usually a browser or mobile app) requests an access token from the authorization server, often through a redirect. The access token is included in the URL fragment of the redirect URI and can be retrieved by the application from the browser. Since the access token is exposed directly to the client, the app must be built to handle the token securely, typically by storing it temporarily and clearing it after use to reduce exposure.
Why it works: It allows the application to receive tokens directly without an intermediate authorization step, simplifying implementations where the security risks are lower.
Note: This method is less secure because tokens are stored in the client, such as a browser, where they are more susceptible to theft.
3. Client credentials grant
Ideal for: Applications needing to access resources under their control, without acting on behalf of a user.
Scenario: An automated backup service that stores data to a cloud storage solution can authenticate using its own credentials, rather than acting on behalf of a user.
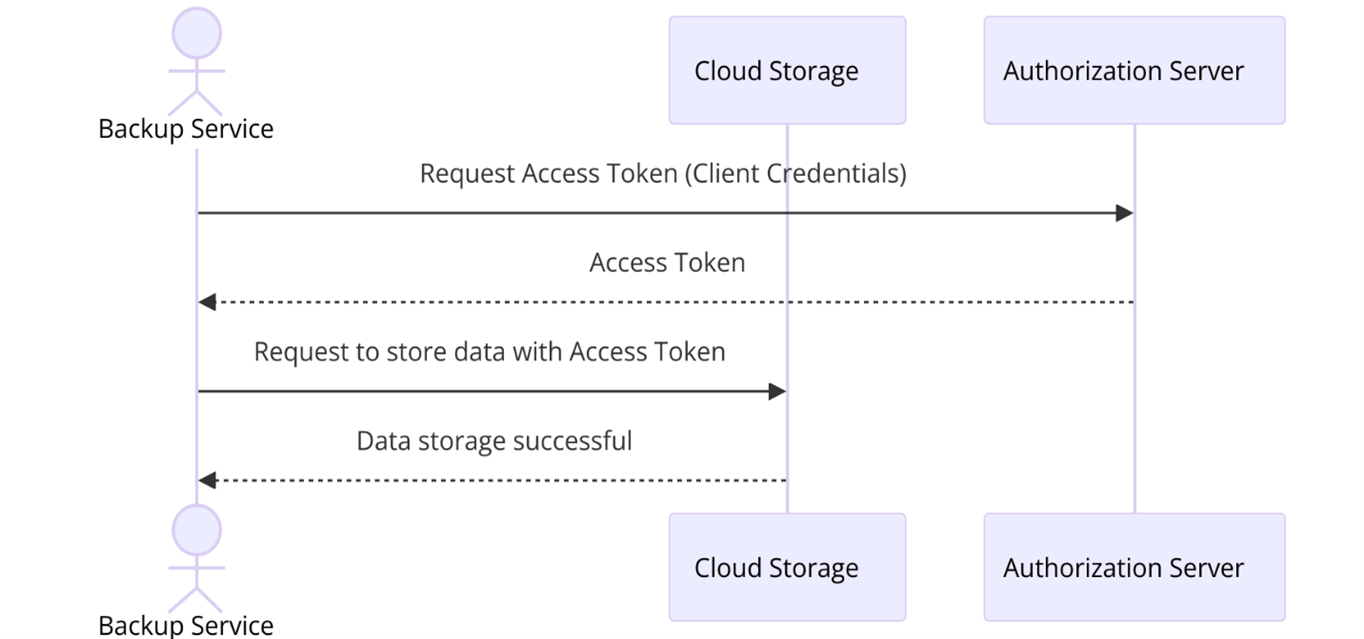
Sequence diagram illustrating the client credential grant OAuth flow for an automated backup service
For client credentials grant type, the key components needed are:
- Client ID and client secret: These are issued by the authorization server and uniquely identify the client application.
- Authorization server: A service that validates the client’s credentials and issues an access token if they are correct.
- Access token: The token is then used to authenticate API requests to a resource server.
Technical setup: The client application must be capable of securely storing the client ID and client secret. It also needs to handle HTTP requests to the authorization server to exchange credentials for an access token, and then attach the token in the Authorization header when making requests to the resource API.
Why it works: This grant type is efficient and straightforward, as it doesn’t involve user interaction, reducing complexity when only machine-to-machine communication is required.
Note: Since this grant type does not involve a user, it’s critical that the client credentials are kept secure.
4. Resource owner password credentials grant
Ideal for: Highly trusted applications, such as those developed by the same entity that manages the resource server.
Scenario: A corporate mobile app that provides employees access to internal systems might use this grant type, as the application is fully trusted.
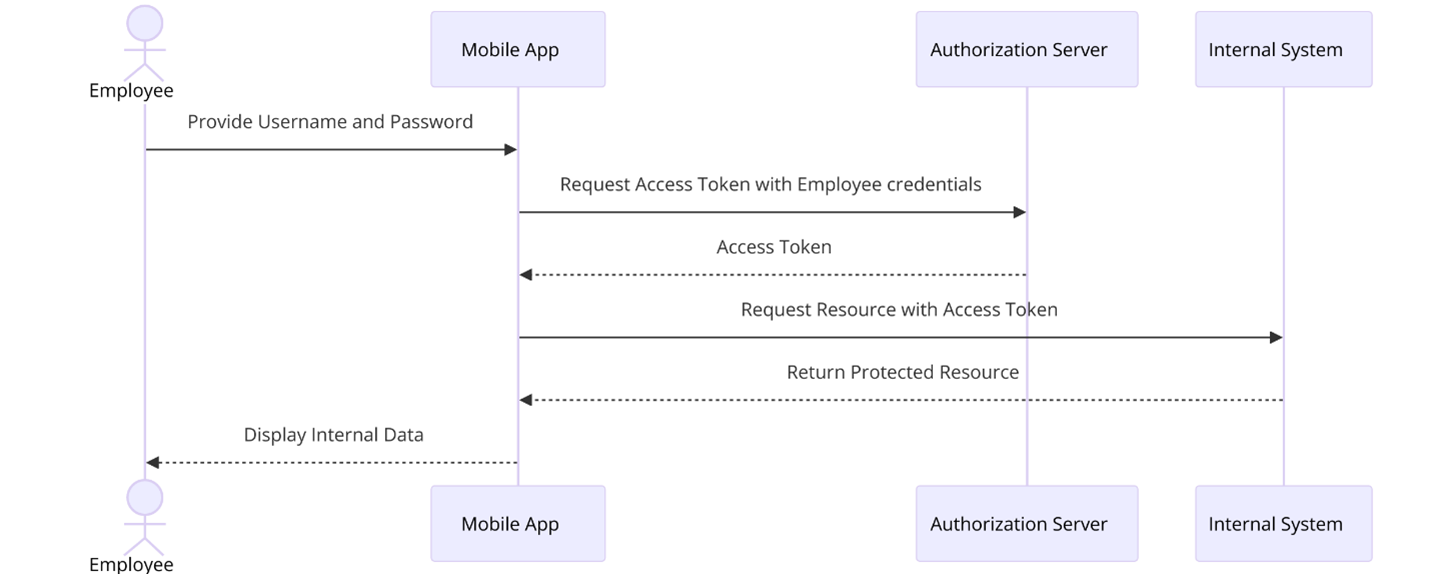
Sequence diagram illustrating the resource owner password credentials grant OAuth flow for a corporate mobile app
For resource owner password credentials grant type, the components required include:
- Username and password: The user’s credentials are directly provided to the client application, which is why this grant type is only used when the client is highly trusted (like first-party applications).
- Client ID and client secret: Similar to other grants, these are used to identify and authenticate the client.
- Authorization server: Validates the user’s credentials and issues an access token.
- Access token: Used by the client to access protected resources on behalf of the user.
Technical setup: The client application must securely handle and transmit the user’s credentials to the authorization server. The app needs to implement robust measures to ensure that the username and password are never exposed or stored insecurely. Once the access token is received, it’s used in subsequent API requests via the authorization header.
Why it works: In trusted environments where the risk of credential exposure is minimal, this grant type simplifies the flow by using the user’s login credentials directly.
Note: This method involves the application handling the user’s credentials, making it less ideal unless the client is completely trusted.
Making the right choice: why the OAuth grant type matters
The choice of grant type should consider the application type, the environment in which it operates, the level of trust with the user, and the security requirements. As developers and security professionals, our goal should be to choose the most secure grant type that fits the use case without compromising the user experience.
Choosing the right OAuth grant type is more than a technical decision—it’s a cornerstone of your application’s security posture.
As we rely increasingly on interconnected services, securing these connections becomes paramount. Failure to do so can lead to data breaches, unauthorized access, and other security mishaps that can severely damage both reputation and trust.
OAuth simplifies secure access, but only when implemented correctly. As you design or audit your application, keep these scenarios in mind to ensure you’re aligning with best practices in API security.
I hope this guide not only aims to clarify how OAuth works but also empower developers to make informed decisions that align with best security practices.
Discover more API security tools and best practices.

