PKI, OCSP/SCVP, CRLDP, DVS, DVE, SV, CA, VA (Validation Authority Suite), HSPD-12, PIV, DHS, DOD, GSA, DOS, TMWD, AXWAY, GSA SSP, OK… If you wonder what all these terms, abbreviations, variations and gyrations mean, you will want to read this post.
Notice I left some three-letter abbreviations out for good reasons!
We will start with PIV and HSPD-12 to continue from my previous blog on APIFriends on two-factor authentication.
HSPD-12
Smart Card Physical and Logical Access all started large scale with HSPD-12. Read more about HSPD-12.
George W. Bush, our 43rd President of the United States, directed on August 27, 2004.
The Homeland Security Presidential Directive 12 is taking a long time for all government agencies to adhere to. Part of the problem, they say from the beginning is that this was an unfunded program. To make a long story short, HSPD-12 required government agencies to come up with a common identification standard for Federal Employees and Contractors. This brought about HSPD-12 PIV Cards for Federal Civilian Agencies and a PIV Standard. DOD calls theirs the CAC card but uses and adheres to the current PIV specifications.
One requirement on an HSPD-12 PIV is that the user receiving the Smart Card PIV Card must have gone through the appropriate background checks, i.e., Secret, Top Secret and whatever type clearance requirement by the agency issuing the smart card. Read more about SecureTransports: Many upgrades make one big success story.
I have what is called an External Certificate Authority ECA Certificate and the only difference between it and the PIV Card is that it doesn’t have the required Background Check. Unfortunately, you also can’t access that much with PIV-I (that’s the ECA Smart Card). However, it is good for someone who likes to test and show how our solution works with the PIV card, especially since everything else is per the standard and is the same thing a DOD or Federal Civilian employee will have when they explore and work with the PKI X509 Digital Certificates.
PIV
There are four certificates on the PIV Card:
- PIV Authentication
- Card Authentication
- Digital Signature
- Encryption
There are optional and mandatory fields required for a PIV Card, and the standards have changed over time. For instance, it’s not expected that PIV Cards have Card Authentication certificate until after September 2019. I know that date has passed but we are talking about the government and when you include all agencies current for now.
So now, hopefully, we understand what PIV, CAC and Smart Card mean and their advantage over usernames and passwords. Let’s move on to how it can be implemented to provide secure validation for physical and logical access using PKI.
PKI
With a solution such as Axway Desktop Validator Standard and Desktop Validator Enterprise, you can control your user authentication and validation for your enterprise and make it manageable so that users usually don’t even realize it is there until they come across a revoked certificate. But how is that different from your typical Microsoft built-in functionality?
To keep this at a high level, Microsoft has what we call Default Validation Options which for Microsoft is crlDP or AIA. Based on the end-users certificate authenticating to a secure website or their domain (i.e., army.mil, dos.gov, doe.gov, dhs.gov, etc.), the PIV authentication checks the certificate and can either download the crl from the distribution point on a certificate or the AIA extension which is to an OCSP Responder or Repeater.
OCSP
OCSP does a 1 to a 2k query to a server that can cache information CRLs can be large and why there is OCSP and sometimes it can be 30-40 MB and imagine all users taking up all your bandwidth for CRLs and why people use OCSP instead.
With Desktop Validator Standard (DVS) Agents installed on the desktop for validating a Domain Controller Certificate or for signed and encrypted e-mail and Desktop Validator Enterprise (DVE) for Domain Controllers and IIS enabled websites to include SharePoint and Citrix Servers, you can have multiple fail-over options. If you have an Apache Server, you can install Server Validator (SV) agent.
If I choose my ORC ECA Certificate under CA Specific Validation Options:
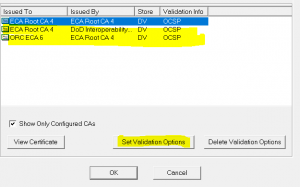
And select my CA and Set Validation Options:
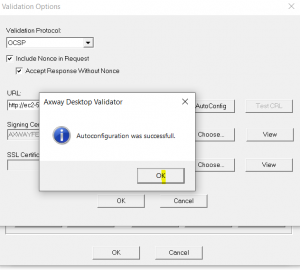
And AutoConfig, if using Axway, you may remember this as Tumbleweed who Axway acquired in 2009.
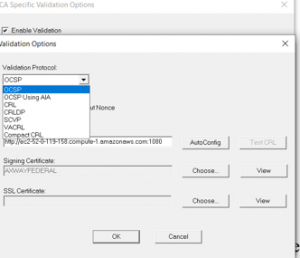
As you can see above, not only can you add multiple OCSP Responders like you will see below, but you can also failback to other protocols as well. It is not uncommon for a Federal Agency PIV Card user or DOD User to have multiple failover to at least two or three different OCSP Responders or Repeaters to ensure there is always a validation response available for mission-critical applications especially. This can also be supported in a closed environment using sneaker net and other capabilities of the OCSP Responders and Repeaters.
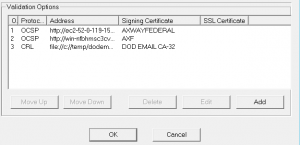
In my next blog, I will introduce the OCSP Server-side that we were just able to complete an easy AutoConfig, whether that is an OCSP Responder or Repeater and give the differences and values of each.
Learn how API authentication and pricing affect stream rank.

