The need for safeguarding file data has never been greater
There’s an old IT saying that nobody notices MFT until something goes wrong. MFT hums along in the background at many enterprises, running on autopilot, out of sight and out of mind.
No need to modernize, update or fix what isn’t broken. Or so goes conventional wisdom at companies resistant to change.
But the cybercriminals know better.
From the pirate’s point of view, MFT is like a fleet of ships sailing between companies with a treasure trove of data. Millions of financial transactions, patient records, and logistical data are transported every day. The crown jewels of your enterprise.
Not all of these ships, however, have been armed, updated and patched to protect their cargo from attackers. Some are more like sitting ducks.
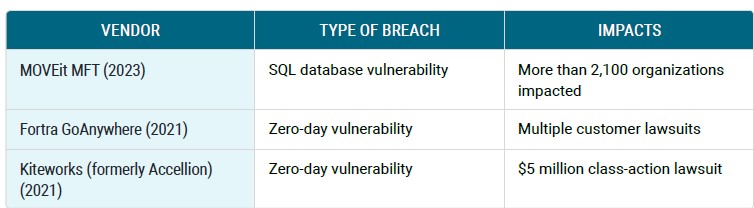
In May of 2023, more than 2,100 organizations (including Amazon) felt the negative impacts of a data breach in the MOVEit MFT service.1 This cyberattack with ransomware exploits led to stolen and leaked customer information from technology, healthcare, financial services, and other industries trusted to protect private data.
It’s clear that even the most prominent players are vulnerable to MFT breaches — and the ripple effects from these breaches can be felt well into the future. The costs to businesses have been enormous due to financial losses and business disruption, reputational damage, regulatory penalties, and class-action lawsuits from partners and customers.
For many businesses, the events of 2023 shifted their focus on MFT from operations to security. As IDC states in its 2024 report, Managed File Transfer: A Critical Capability in Need of Critical Updates: “Organizations need a multi-tactic approach that is proactive and strategic to improve MFT security.”
This Axway guide is designed to help you assess the current state of your MFT security strategy against a background of growing threats. Follow these steps and recommendations to adopt the best practices, technology solutions, policies, and processes you need to build an unbreachable fortress around your MFT operations.
Keep This Guide Handy – Download Now
The risks of MFT data breaches | MFT takes place at the edge of your enterprise network, a dangerous place where the stakes are high and intruders look for entry.
↑ 70 million people negatively impacted by MFT data breaches
↑ 80% breaches involving compromised user accounts
↑ 2,100 organizations damaged by MOVEDit breach
1. Create a culture of MFT security
All data security regulations and security standards recommend or mandate creating a culture of security. This helps integrate security into every part of your organization, reducing vulnerabilities and fostering a proactive approach to safeguarding data.
Axway recommends:
![]() Focus on employee awareness and training.
Focus on employee awareness and training.
It’s an unfortunate reality: people tend to be the weakest security link. Sometimes it’s a matter of using weak passwords. Other times, users can share sensitive information without knowing it — including through phishing attacks. Beyond technical MFT security aspects, there’s the need to prioritize training and strong security management policies.
- Clearly outline password policies and multi-factor authentication standards
- Make sure employees can detect phishing-style attacks via email
- Ensure a basic understanding of access controls and data handling
- Regularly review these processes and test them
![]() Reduce human error.
Reduce human error.
Security teams may be overwhelmed by the volume of alerts and tasks. Automation can take care of routine security tasks, like updating encryption keys, rotating access credentials, or enforcing security policies based on real-time conditions. This reduces the possibility of human error, ensures that security measures are consistently applied, and improves the overall security of MFT operations.
![]() Establish clear security policies and procedures.
Establish clear security policies and procedures.
Develop and distribute clear, easy-to-understand security policies that explain the expectations and procedures for secure file transfers. These policies need to cover all aspects of your MFT security, including encryption, authentication, access control, and incident response. Reinforce the idea that security policies must be followed by everyone.
![]() Promote cross-functional collaboration.
Promote cross-functional collaboration.
Work together with departments like to ensure that MFT security is aligned with company-wide initiatives, changing regulatory requirements, and best practices. Make security part of all MFT-related projects, including product development, vendor management, and systems integrations. This ensures that security is baked into projects from the beginning.
2. Keep software up to date
Keeping your MFT software updated is essential for safeguarding your sensitive data, ensuring system reliability, and maintaining compliance with security regulations. Patches and updates are your first line of defense against known vulnerabilities, malware, ransomware, and emerging threats.
Despite these benefits, many companies still face barriers that keep them from making upgrades and patches in a systematic way. These include concerns about operational disruptions, limited IT resources, compatibility issues, and a lack of awareness of the security risks associated with outdated software.
Companies that fall behind in their patching cycles risk being caught in a downward spiral in which they fall many patches behind and can’t catch up without significant business disruption. This can also knock them out of support with trading partners that are staying up to date and using updated communication ciphers. It becomes imperative for these companies to break the cycle of declining security by modernizing their MFT software.
Ensuring that MFT solutions are consistently updated with the latest security patches and software enhancements is another key step; this is akin to maintaining the system’s health to ward off potential cyberthreats.
Axway recommends:
![]() Modernize MFT software architecture.
Modernize MFT software architecture.
You need the right software infrastructure to support high availability and zero-down-time updates (ZDU) and maintenance.
![]() Deploy an automated patch management system.
Deploy an automated patch management system.
The system will regularly check for and apply updates, alerting you to updates that need to be made.
![]() Implement and adhere to a change management process.
Implement and adhere to a change management process.
Formalize the steps by which you monitor, control, and document software updates and patches.
3. Choose the right software architecture for Zero Trust security
When it comes to MFT, security is no longer about simply guarding the perimeter of your network. In today’s landscape of remote work, cloud computing, and hybrid environments, companies need a Zero Trust security model in which no one — whether inside or outside the network — is trusted by default.
Zero Trust is particularly important for MFT operations, which face on the internet and extend to your ecosystem partners. To build an effective security posture, you need modern software architecture that supports Zero Trust policies and best practices across multiple environments and clouds.
Axway recommends:
![]() Enforce least-privilege access.
Enforce least-privilege access.
Under Zero Trust, users, devices, and systems only get the minimal access necessary to perform their tasks. This means setting permissions so that users can only transfer specific files or access certain systems, reducing the risk of unauthorized access. Even if a user’s credentials are compromised, the scope of potential damage is minimized.
![]() Strengthen Identity and Access Management (IAM).
Strengthen Identity and Access Management (IAM).
Every user, device, and system must be authenticated and authorized before being allowed access to resources. Use strong authentication methods such as multi-factor authentication (MFA), and role-based access control (RBAC) to ensure that only authorized users can initiate or receive file transfers. Take a whitelist approach that allows access only to known and named individuals — not a blacklist approach that can leave data vulnerable to unknown threats.
![]() Ensure end-to-end encryption.
Ensure end-to-end encryption.
Zero Trust dictates that all data be encrypted, both in transit through the use of secure protocols (SFTP, FTPS) and at rest, including archived and stored data. Use automation to enforce encryption policies, ensuring that files and data are encrypted based on predefined rules.
4. Integrate seamlessly with internal and third-party tools and systems
The goal of this guide is to make MFT into an unbreachable fortress, but not an island. To the contrary, strong MFT security depends on tight integration with your organization’s broader security systems and policies.
The current focus on MFT security makes it a necessity, but also an opportunity for your MFT team to become a leader in shaping your organization’s security posture — not an outsider or follower.
To make that happen, you need modern, API-driven software that integrates seamlessly with your IT operations systems and tools for data breach detection, mitigation, and repair.
Axway recommends:
![]() Combine visibility into MFT operations with automation and real-time alerts.
Combine visibility into MFT operations with automation and real-time alerts.
Automation kicks in by immediately responding to alerts (e.g., blocking access, quarantining files, or locking user accounts) while your team takes steps for further investigation. In the event of a breach or suspicious activity, your MFT solution needs to provide the data needed to quickly understand the scope of the incident. Automated incident response immediately mitigates the threat, and security teams can access logs and historical data to quickly restore the system to a secure state.
![]() Connect to Security Information and Event Management (SIEM) systems.
Connect to Security Information and Event Management (SIEM) systems.
These systems enable you to monitor and collect logs generated by file transfer activities, alerting you in real time to potential security threats as they happen. Many SIEM systems now employ AI (machine learning) to identify abnormal patterns in MFT logs. While keeping you alert to threats, these systems produce and store the logs and audit trails you need to stay in compliance with regulations like GDPR, HIPAA, SOX, and PCI DSS. They can also generate compliance reports for internal management and regulators. SIEM systems can correlate events from your MFT environment with other security tools like firewalls, intrusion detection systems, and endpoint protection solutions. They can also provide context to events by grouping related events together.
![]() Integrate with internal backup and disaster recovery solutions.
Integrate with internal backup and disaster recovery solutions.
Ensure that your file transfers are securely backed up and can be restored in case of an incident. Cloud-based backup systems allow you to store data in multiple locations, further reducing the risk of data loss.
![]() 4 pitfalls to watch out for in MFT operations
4 pitfalls to watch out for in MFT operations
- Your production environment isn’t using the latest version and lacks essential security patches
- Your MFT is out of scope for incident management processes and tools
- You haven’t systematically adopted RBAC or encryption across your file transfers
- You don’t have disaster recovery or backup plans in place for MFT breaches
5. Seek out an MFT vendor with a strong security focus
As IDC puts it, “Companies must collaborate with vendors dedicated to the continuous development and update of their solutions.”7 Building an unbreachable fortress around your MFT operations requires a vendor with deep security expertise evidenced by both its software solutions and its internal programs and commitments.
Axway recommends:
![]() Software solutions designed for security and compliance in modern, web-facing MFT environments
Software solutions designed for security and compliance in modern, web-facing MFT environments
- Proven success keeping customers secure in your industry
- Certified security experts on staff
- Strong internal security posture and programs based on zero-sum principles
- User groups offering support and knowledge on security issues
- Managed services options, enabling you to overcome skills gaps and reduce costs by delegating all or part of your MFT security to an expert service provider
Does your vendor make security part of everything they do?
![]() COMPLIANCE
COMPLIANCE
Industry-specific regulations (e.g., HIPAA) | NIST 800-53 | Privacy regulations (EU GDPR) | Public cloud providers shared responsibility models | SecNumCloud | PCI DSS
![]() EXPERTISE
EXPERTISE
Staffed with certified security engineers | Maintains security roadmap | Active in user groups, advisory boards | Sponsors public online security training | Develops and executes on Zero Trust initiatives
![]() SECURITY POSTURE AND TRANSPARENCY
SECURITY POSTURE AND TRANSPARENCY
Strong track record addressing critical or high vulnerabilities | Integrates security in software bill of materials | Delivers security refactoring features in each release | Makes PenTests auditable | Adheres to public disclosure policy
![]() SECURITY PROGRAMS
SECURITY PROGRAMS
Information Security Management System (ISMS) | Cloud Services certification | Software security red/blue teams | Secure Software Development Lifecycle (SSDLC) program
MFT data breaches rock the industry
Since 2021, several notable data breaches have proved costly to MFT vendors and their customers.
6. Why choose Axway for MFT security?
Axway is committed to your security through our culture and processes. We offer an enterprise-grade MFT solution, SLAs of up to 99.99%, and follow-the-sun support.
Axway MFT solutions set the gold standard for keeping your MFT operations efficient, compliant, and secure. Benefits include:
![]() Solutions designed for security
Solutions designed for security
Software providing end-to-end encryption, MFA, data integrity checks, and continuous compliance
![]() Scalability and flexibility
Scalability and flexibility
Supports cloud, hybrid, and on-prem deployments and offers managed service options
![]() Monitoring, automation, audit
Monitoring, automation, audit
Delivers and automates real-time monitoring, logging, patching, and compliance
![]() Integration with internal and external systems
Integration with internal and external systems
Seamless integration with enterprise and third-party security systems and tools for data breach detection, mitigation, recovery and repair
![]() Availability and reliability
Availability and reliability
Resilient, flexible architecture, including containerization options for high availability and zero-downtime maintenance
![]() Unmatched expertise
Unmatched expertise
Proven track record delivering secure file transfer solutions to leaders in finance, healthcare, retail, manufacturing, government and other industries
![]() Internal security focus
Internal security focus
Certified security experts, strong security posture, company-wide programs, compliance support, security-based product development, user groups, and more
Ready to make your MFT operations an unbreachable fortress?

Follow us on social