In part one of this series, we covered the capabilities of Axway SecureTransport SecureTransport ICAP integration with third-party Antivirus and DLP software and some details on its configuration.
This second installment will cover a simple way to validate and demonstrate that the AV scanning is working.
A simple way to validate AV scanning
This exercise will demonstrate how ICAP AV scanning works with a simple example by using the SecureTransport Web Client and curl from a Linux command line.
We will first disable the ICAP Server in SecureTransport and upload the eicar virus files from the Linux command line to show the behavior when an incoming virus file is uploaded without any scanning enabled. (Hint: Nothing happens, the upload is successful.)
Next, we will attempt to download the file we just uploaded from a SecureTransport Web Client on a PC with some AV software installed such as McAfee, Norton Security, or Windows Defender.
What we will observe is that the file will be successfully downloaded by the SecureTransport Web Client but then our desktop AV software will scan it, recognize it as a virus and quarantine the file. This proves the file is a virus file but without AV scanning enabled in SecureTransport, SecureTransport will not block it.
We will then validate Outbound scanning in SecureTransport by enabling the ICAP Server in SecureTransport and attempt to download the file with the SecureTransport Web Client again. We will observe that the SecureTransport Web Client blocks the download from occurring because the AV scan in SecureTransport identifies the file as a virus and blocks the download.
You can also attempt to download the file via another protocol client such as SFTP, FTP, etc. And in each case, the transfer will not be successful. This demonstrates that SecureTransport successfully scanned an outbound file.
Next step
Next, we will validate Inbound scanning by attempting to upload the eicar files with the SecureTransport Web Client, an SFTP client, or both.
Let’s start by setting the ICAP Server settings to allow BOTH incoming and outgoing scans and to scan all files by removing any filters:
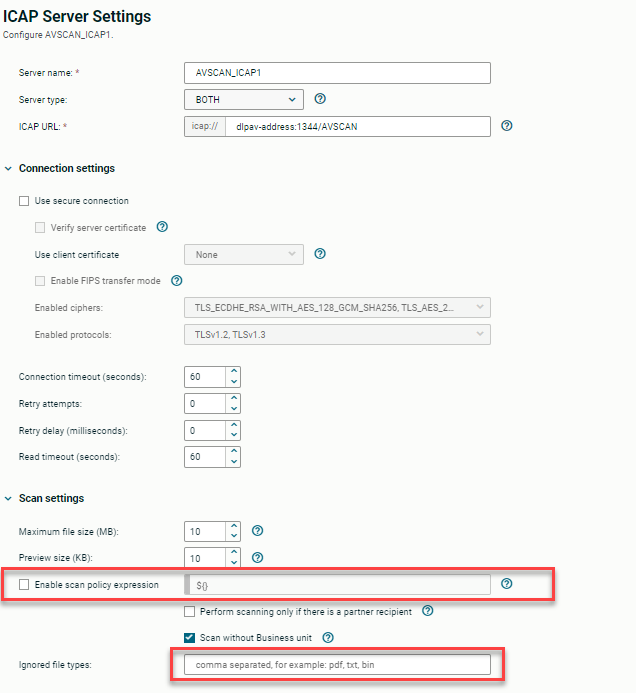
Steps:
- Disable the ICAP Server.
- Go to Setup/ICAP Settings.
- Select the ICAP Server and click Disable.
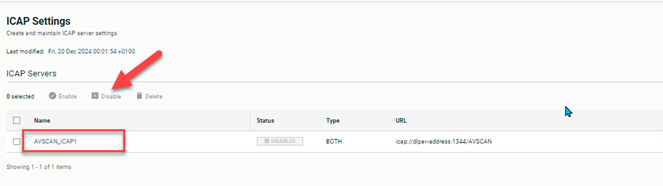
- Upload a couple of infected files with AV Scan disabled.
- curl -k “sftp://<SecureTransport Hostname or IP>:<SecureTransport SFTP port>” –user “alice:alice” -T eicar_com.zip where alice:alice is to be replaced by your SecureTransport user name and password.
- Confirm that the file is infected.
- Download the virus file via ST Web Client. Observe that the SecureTransport Web Client allows the file to be downloaded.
- Observe that the desktop AV software quarantines the file after it’s downloaded confirming that it’s in fact a virus file.
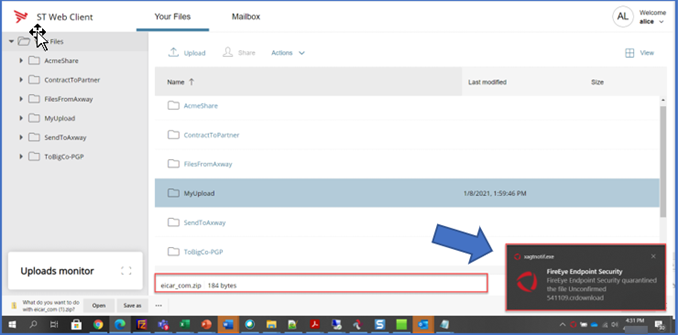
- What we have observed is that without AV scanning enabled within SecureTransport, we were able to upload a virus file TO SecureTransport and then download that same virus FROM SecureTransport. The virus was captured by the desktop AV software after a successful download from SecureTransport.
- Enable the ICAP Server.
- Go to Setup/ICAP Settings.
- Select the ICAP Server and click Enable.
Outbound File AV Scanning Validation
- From the SecureTransport Web Client, attempt to download the virus file that was previously uploaded.
SecureTransport blocks the file from being downloaded via the SecureTransport Web Client (or via any download protocol).
SecureTransport Web Client:
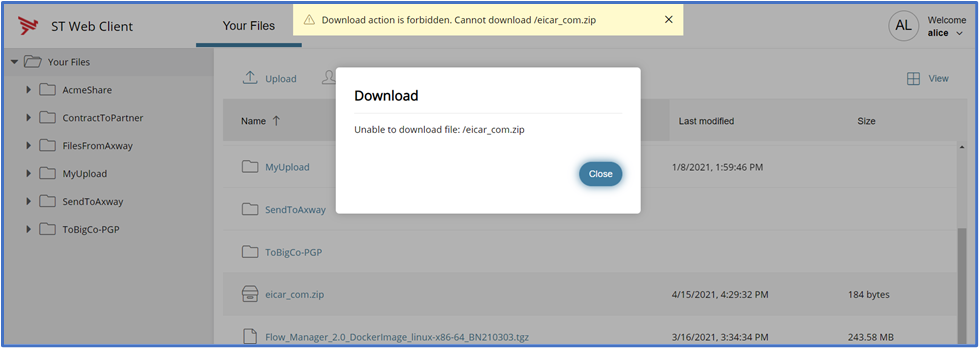
And if we attempt the download via using the curl command on Linux we get the following result…
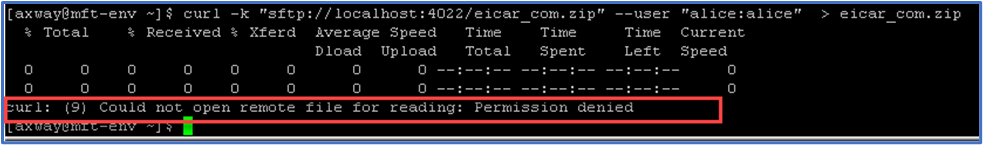
An error will appear for the download attempt in File Tracking.
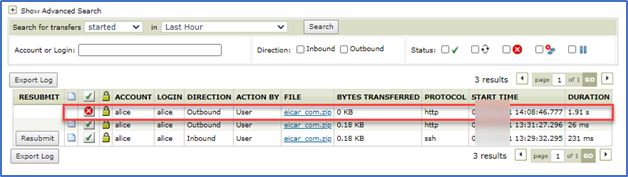
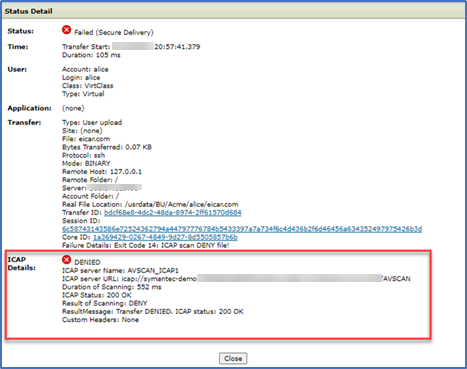
If we drill down into the hyperlinks on the error, we will see the details…
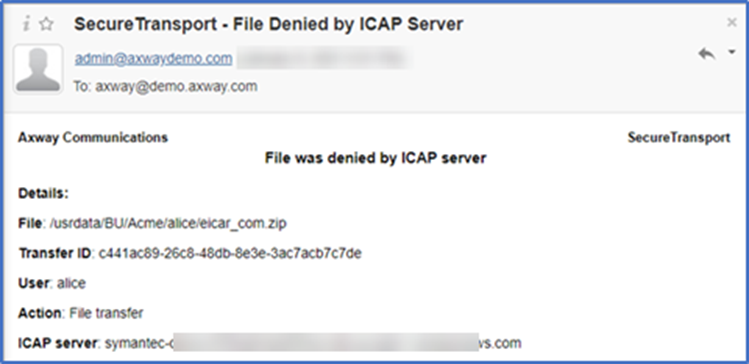
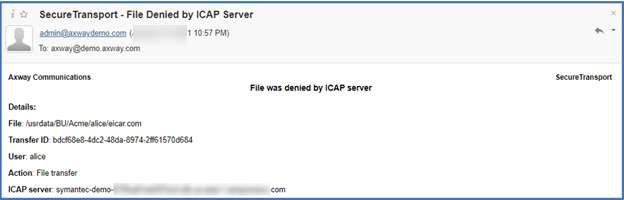
And if we have enabled email notifications in the SecureTransport ICAP Server settings, we will receive an email notification…
Note that if the AV scan did not find a virus, the download would be successful and the file status details in SecureTransport File Tracking would be similar to…
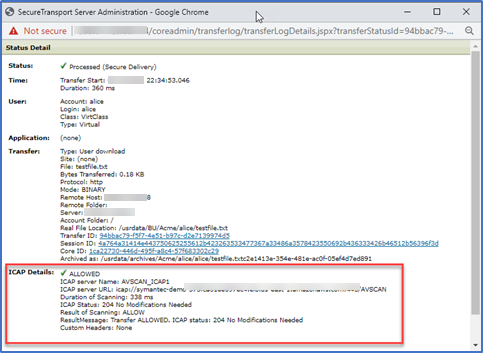
Inbound File AV Scanning Validation
- With the ICAP server still enabled, upload one of the sample virus files via the SecureTransport Web Client.
Observe that when using the SecureTransport Web Client, the file upload will be blocked, and the Uploads monitor will show the failed upload…
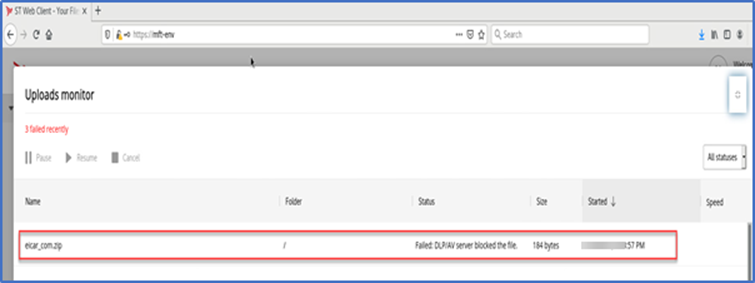
Tip: To validate the user experience of an upload using the SecureTransport Web Client, I used the browser on the Linux virtual machine desktop where I downloaded the eicar file so that the desktop AV software on my Windows workstation would not block it.
If we use any other protocol client such as FTP or SFTP to upload the infected file, the upload will complete successfully from the perspective of the protocol client. However, the file will never appear in a listing of the folder because it is hidden by SecureTransport until after the successful completion of the ICAP AV scan. If the scan fails, the file is automatically deleted from the folder.
Regardless of what client is used, if the ICAP AV scan fails an error will appear in File Tracking…
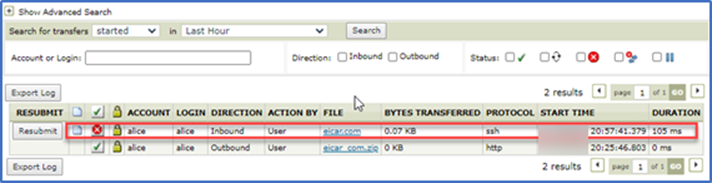
Drilling down on the failure in File Tracking we can see the details…
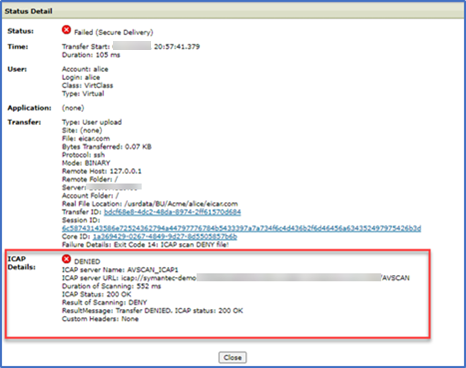
Additional details can be found in the SecureTransport Server Log…
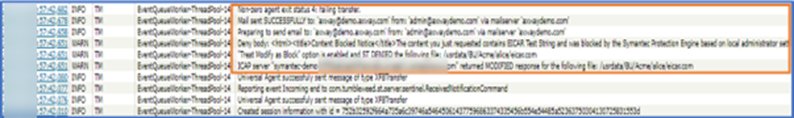
And an email notification will be sent if enabled…
Note that if the AV scan did not find a virus, the upload would be successful, and the file status details in SecureTransport File Tracking would include an ICAP status message.
We have now successfully validated both inbound and outbound AV scanning using the ability of Axway SecureTransport to integrate with a third-party AV or DLP solution via ICAP.
By leveraging this capability you can ensure that files entering or leaving your organization don’t contain viruses or sensitive information helping ensure the security and reputation of your organization.
In the next installment, we will discuss some considerations when working with PGP encrypted data.

