What happens when you hack the infotainment system of a car and then sell your hack as a service? What happens when you do that but forget to defend yourself?
You get hacked.
As a member of the of Axway Product Security team, I explained to the audience at DefCamp 2019 security conference how I broke into what I call “Hack as a Service.” I used a chained attack technique, abusing different weaknesses in the services offered by an anonymous hacker who was “selling” a utility application for Honda infotainment systems. I showcased the whole process, step by step, including the incentives but also the tools I used, along with the (most important): The how and why’s that his attack was successful.
Because security research is fun but, in the end, we must learn something from it, right? I explained how a mix of weak password policy, lack of brute force attack mitigation, security misconfiguration, security best practices ignorance plus a broken application license mechanism can break your business. While the full presentation video can be watched on YouTube, here is a summary of my talk:
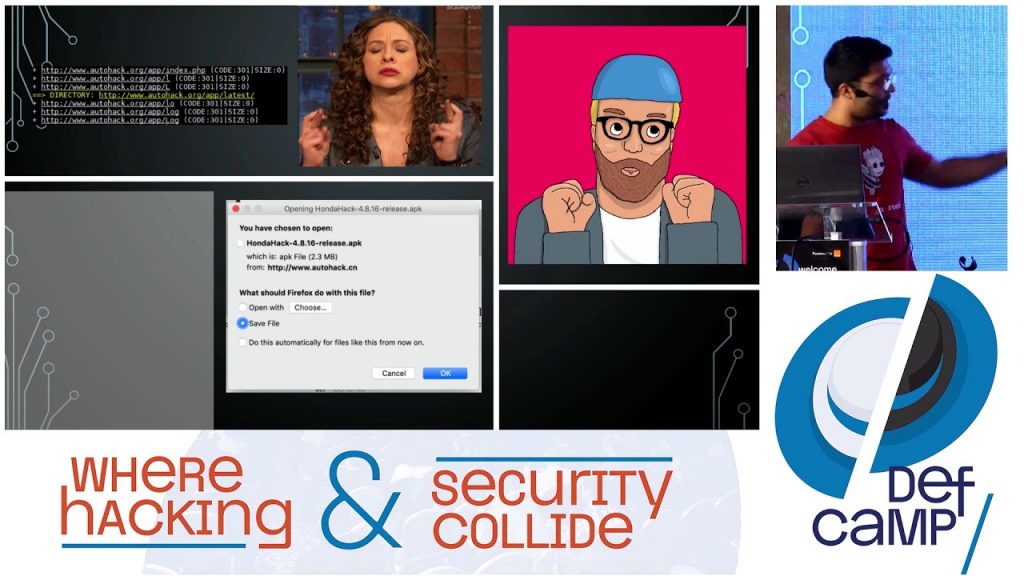
An anonymous website hosting a JavaScript Android exploit meant to root the Android device and install an application called “Honda Hack.” This website was hosting payloads for the latest infotainment systems of Honda vehicles which are running Android operating systems. Legitimate users would have to pay some money in exchange for an authorization code that would allow the exploit to run and the Honda Hack application to be installed on the device.
Chapter I: Content Discovery
Phase 1 of the attack was brute-forcing resources URLs in order to find hidden but available content on the website. The main purpose was to find the APK file that was supposed to be hosted on the server. For such scenarios, tools like dirb or Burp Proxy are handy.
Chapter II: Brute-forcing password-protected resources
Even though phase 1 was successful and the APK file was retrieved, I could not have it installed on the infotainment system device without rooting it. The JavaScript payload for rooting the device was protected by a server-side enforced authorization code. Server-side validation is the right way to do it, isn’t it? The only problem is that the code’s length was being checked at the client-side and that provided enough clues to perform a brute-force attack on it. This phase concluded with uncovering two valid authorization codes in a fairly short amount of time.
Chapter III: Reverse engineering the Android application
Having the app installed revealed that it was asking for a key in order to upgrade to the Pro version and use all the features. For getting the key, I performed both static and dynamic analysis of the application and reverse-engineered the key validation system. This attack was facilitated by several mistakes that the developer did, and I explained them during the talk. After all, the entire attack chain was successful because of weaknesses identified in each component of the system: infrastructure, web application, APK source code.
During my presentation, the audience had the chance to hear this story taken from the real world and it was well-received. One of the main benefits of Infosec Community is that we can exchange ideas, share knowledge and experience that can be further applied in our daily job, ending up with a more secure digital world.
READ MORE: 8 ways to Help Keep Ransomware from Holding your Digital Files Hostage
DefCamp is the most important annual conference on Hacking & Information Security in Central Eastern Europe. Each year it takes place in Bucharest. This year it celebrated its 10th edition. This conference has grown rapidly over the years and the numbers speak for themselves. This edition of DefCamp brought together over 2,000 decision-makers, security specialists, entrepreneurs, developers, academic, private and public sectors.
A funny fact: the very first edition of DefCamp had as many attendees as this year’s edition had speakers.
Each year, Axway has a strong presence at the most important security conferences all over the world. Axway security experts are active members of the Infosec community, participating with content, code and engagement in CTF competitions.
Learn more about API Security, checking it twice.
Follow us on social